Next: GNU Lesser General Public License, Previous: Description of the Self-Tests, Up: The Libgcrypt Library [Contents][Index]
Appendix B Description of the FIPS Mode
This appendix gives detailed information pertaining to the FIPS mode. In particular, the changes to the standard mode and the finite state machine are described. The self-tests required in this mode are described in the appendix on self-tests.
B.1 Restrictions in FIPS Mode
If Libgcrypt is used in FIPS mode, these restrictions are effective:
- The cryptographic algorithms are restricted to this list:
- GCRY_CIPHER_AES128
AES 128 bit symmetric encryption.
- GCRY_CIPHER_AES192
AES 192 bit symmetric encryption.
- GCRY_CIPHER_AES256
AES 256 bit symmetric encryption.
- GCRY_MD_SHA1
SHA-1 message digest.
- GCRY_MD_SHA224
SHA-224 message digest.
- GCRY_MD_SHA256
SHA-256 message digest.
- GCRY_MD_SHA384
SHA-384 message digest.
- GCRY_MD_SHA512
SHA-512 message digest.
- GCRY_MD_SHA3_224
SHA3-224 message digest.
- GCRY_MD_SHA3_256
SHA3-256 message digest.
- GCRY_MD_SHA3_384
SHA3-384 message digest.
- GCRY_MD_SHA3_512
SHA3-512 message digest.
- GCRY_MD_SHA1,GCRY_MD_FLAG_HMAC
HMAC using a SHA-1 message digest.
- GCRY_MD_SHA224,GCRY_MD_FLAG_HMAC
HMAC using a SHA-224 message digest.
- GCRY_MD_SHA256,GCRY_MD_FLAG_HMAC
HMAC using a SHA-256 message digest.
- GCRY_MD_SHA384,GCRY_MD_FLAG_HMAC
HMAC using a SHA-384 message digest.
- GCRY_MD_SHA512,GCRY_MD_FLAG_HMAC
HMAC using a SHA-512 message digest.
- GCRY_MD_SHA3_224,GCRY_MD_FLAG_HMAC
HMAC using a SHA3-224 message digest.
- GCRY_MD_SHA3_256,GCRY_MD_FLAG_HMAC
HMAC using a SHA3-256 message digest.
- GCRY_MD_SHA3_384,GCRY_MD_FLAG_HMAC
HMAC using a SHA3-384 message digest.
- GCRY_MD_SHA3_512,GCRY_MD_FLAG_HMAC
HMAC using a SHA3-512 message digest.
- GCRY_MAC_CMAC_AES
CMAC using a AES key.
- GCRY_PK_RSA
RSA encryption and signing.
- GCRY_PK_ECC
ECC encryption and signing.
Note that the CRC algorithms are not considered cryptographic algorithms and thus are in addition available.
- RSA key generation refuses to create and use a key with a keysize of less than 2048 bits.
- The
transient-keyflag for RSA key generation is ignored. - Support for the VIA Padlock engine is disabled.
- FIPS mode may only be used on systems with a /dev/random device or with a getentropy syscall. Switching into FIPS mode on other systems will fail at runtime.
- Saving and loading a random seed file is ignored.
- The DRBG style random number generator is used in place of the large-pool-CSPRNG generator.
- The command
GCRYCTL_ENABLE_QUICK_RANDOMis ignored. - Message digest debugging is disabled.
- All debug output related to cryptographic data is suppressed.
- On-the-fly self-tests are not performed, instead self-tests are run before entering operational state.
- The function
gcry_set_allocation_handlermay not be used. In FIPS mode this function does not have any effect, because FIPS has requirements for memory zeroization. - The digest algorithm MD5 may not be used.
- The signatures using SHA-1 digest algorithm may not be used.
- In FIPS mode the command
GCRYCTL_DISABLE_SECMEMis ignored. - A handler set by
gcry_set_outofcore_handleris ignored. - A handler set by
gcry_set_fatalerror_handleris ignored.
Note that when we speak about disabling FIPS mode, it merely means
that the function gcry_fips_mode_active returns false; it does
not mean that any non FIPS algorithms are allowed.
B.2 FIPS Finite State Machine
The FIPS mode of Libgcrypt implements a finite state machine (FSM) using 8 states (see Table B.1) and checks at runtime that only valid transitions (see Table B.2) may happen.
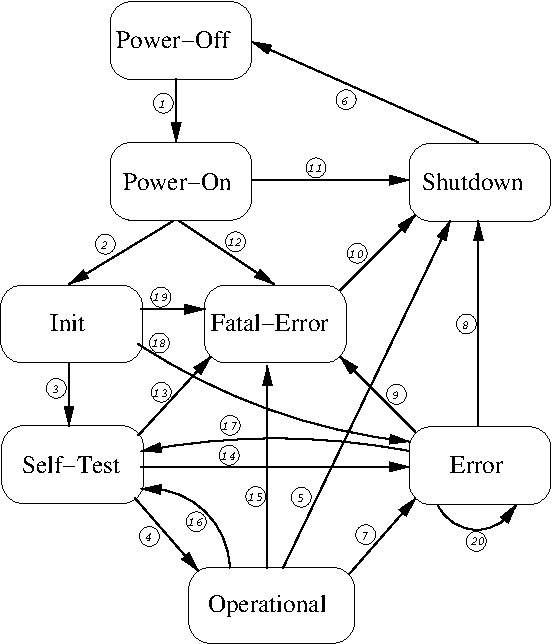
Figure B.1: FIPS mode state diagram
States used by the FIPS FSM:
- Power-Off
Libgcrypt is not runtime linked to another application. This usually means that the library is not loaded into main memory. This state is documentation only.
- Power-On
Libgcrypt is loaded into memory and API calls may be made. Compiler introduced constructor functions may be run. Note that Libgcrypt does not implement any arbitrary constructor functions to be called by the operating system
- Init
The Libgcrypt initialization functions are performed and the library has not yet run any self-test.
- Self-Test
Libgcrypt is performing self-tests.
- Operational
Libgcrypt is in the operational state and all interfaces may be used.
- Error
Libgrypt is in the error state. When calling any FIPS relevant interfaces they either return an error (
GPG_ERR_NOT_OPERATIONAL) or put Libgcrypt into the Fatal-Error state and won’t return.- Fatal-Error
Libgcrypt is in a non-recoverable error state and will automatically transit into the Shutdown state.
- Shutdown
Libgcrypt is about to be terminated and removed from the memory. The application may at this point still run cleanup handlers.
Table B.1: FIPS mode states
The valid state transitions (see Figure B.1) are:
1Power-Off to Power-On is implicitly done by the OS loading Libgcrypt as a shared library and having it linked to an application.
2Power-On to Init is triggered by the application calling the Libgcrypt initialization function
gcry_check_version.3Init to Self-Test is either triggered by a dedicated API call or implicit by invoking a Libgrypt service controlled by the FSM.
4Self-Test to Operational is triggered after all self-tests passed successfully.
5Operational to Shutdown is an artificial state without any direct action in Libgcrypt. When reaching the Shutdown state the library is deinitialized and can’t return to any other state again.
6Shutdown to Power-Off is the process of removing Libgcrypt from the computer’s memory. For obvious reasons the Power-Off state can’t be represented within Libgcrypt and thus this transition is for documentation only.
7Operational to Error is triggered if Libgcrypt detected an application error which can’t be returned to the caller but still allows Libgcrypt to properly run. In the Error state all FIPS relevant interfaces return an error code.
8Error to Shutdown is similar to the Operational to Shutdown transition (5).
9Error to Fatal-Error is triggered if Libgrypt detects an fatal error while already being in Error state.
10Fatal-Error to Shutdown is automatically entered by Libgcrypt after having reported the error.
11Power-On to Shutdown is an artificial state to document that Libgcrypt has not yet been initialized but the process is about to terminate.
12Power-On to Fatal-Error will be triggered if certain Libgcrypt functions are used without having reached the Init state.
13Self-Test to Fatal-Error is triggered by severe errors in Libgcrypt while running self-tests.
14Self-Test to Error is triggered by a failed self-test.
15Operational to Fatal-Error is triggered if Libcrypt encountered a non-recoverable error.
16Operational to Self-Test is triggered if the application requested to run the self-tests again.
17Error to Self-Test is triggered if the application has requested to run self-tests to get back into operational state after an error.
18Init to Error is triggered by errors in the initialization code.
19Init to Fatal-Error is triggered by non-recoverable errors in the initialization code.
20Error to Error is triggered by errors while already in the Error state.
Table B.2: FIPS mode state transitions
B.3 FIPS Miscellaneous Information
Libgcrypt does not do any key management on itself; the application
needs to care about it. Keys which are passed to Libgcrypt should be
allocated in secure memory as available with the functions
gcry_malloc_secure and gcry_calloc_secure. By calling
gcry_free on this memory, the memory and thus the keys are
overwritten with zero bytes before releasing the memory.
For use with the random number generator, Libgcrypt generates 3
internal keys which are stored in the encryption contexts used by the
RNG. These keys are stored in secure memory for the lifetime of the
process. Application are required to use GCRYCTL_TERM_SECMEM
before process termination. This will zero out the entire secure
memory and thus also the encryption contexts with these keys.